I’ve already made some changes to the Six Pillars of Health cheat sheet. I will keep the most updated version here.
Six Pillars of Health cheat sheet
Posted: April 18, 2019 by IntentionalPrivacy in Handling job stress betterTags: diet, health, job stress, mental health
Avoiding Google tracking
Posted: April 4, 2019 by IntentionalPrivacy in privacyTags: Big Data, Chrome, data privacy, DuckDuckGo, Firefox, privacy, privacy tips, search engine privacy, security
I read a couple of interesting articles recently on how to cut down on Google tracking someone’s actions. I have used the DuckDuckGo browser for a long time and Signal, but it’s easy to put one’s head in the sand and ignore the rest. Check them out! How to Live Without Google and What does Google know about me?
A Cautionary Tale
Posted: April 1, 2019 by IntentionalPrivacy in Handling job stress betterTags: diet, health, job stress, mental health
Stress is a component of everyone’s life. Stress can be good; making us feel alive and excited about life. Bad stress comes from chronic or numerous acute stress situations. Chronic stressors for information security professionals can include working long hours, burnout, frequent travel, inadequate sleep, poor food choices, an unhappy or incomplete home life, imposter syndrome, inadequate resources to do their jobs properly, a lack of support by management and other stakeholders, and trying to keep up with new developments in the industry. While acute stress—sometimes referred to as the “fight or flight” response—can be motivating, constantly reacting to events in emergency mode instead of proactively looking for solutions can lead to becoming an adrenaline junkie.
Managing stress poorly can lead to major health problems such as depression, heart attack, stroke, and autoimmune diseases. It can even impact your job performance!
A couple of years ago, I let bad stress take over my life, and I paid for it with health problems. Last week, I spoke at BSides Austin in the Mental Health Hackers Village. My talk was called “Using the ‘six pillars of health’ to mitigate stress and emotional malware.” I put together a cheat sheet that contains some tips on how to live a less stress-filled life.
Recently, I was taking a class on how to attack network protocols, when I realized there was not a lot of documentation on using hex dumps. So I wrote this Hexdump Primer. I would appreciate any comments.
Carrots and Sticks! How to improve your security culture …
Posted: November 3, 2018 by IntentionalPrivacy in Compliance, HIPAA - HITECH, Privacy, Security or Privacy Initiatives, Tips, VulnerabilitiesTags: Compliance, proactivity, security breach
Originally written for Third Rock
Sticks
Just like technology controls, administrative controls work better when they are layered. Almost every organization has an administrative control “stick” in the form of policies. The purpose of policies is to explain the rules as well as the consequences if the rules are not followed.
But do the employees really understand what every policy means? Some may be too embarrassed to ask for an explanation if they do not understand a particular policy. Another issue with policies may occur if an employee does not remember what they agreed to five minutes after they handed in their signed policy understanding statement.
Carrots
This is where a security awareness program can help improve an organization’s security culture enormously. It does not have to be expensive to be effective. The program will also be more effective if security awareness training can involve employees. Here are some techniques:
- Make security training interactive. Use only a small number of PowerPoint slides, tell relevant stories, and keep it short and engaging.
Look for ways to make security important to an employee’s personal life; for instance, show how they can better protect their families online. Employees who practice good security hygiene at home will be better at understanding and implementing security at work.
People learn different ways! The more types of senses used during the training, the better it will be remembered by the audience. Break up the training monotony with focus groups, table-top exercises, and question-and-answer sessions. Instead of having a once-a-year marathon, have sessions monthly or even quarterly. If they are held during lunch make sure you provide food.
There are several places to find resources online. StaySafeOnline.org is one example; they have tip sheets and videos for all age groups and even for businesses. The FTC also offers resources at their Stick with Security blog.
- Encourage employees to turn in social engineering attempts. Give a small reward, such as a coffee cup, to the first employee who turns in a security issue, such as a phishing email or a social engineering phone call. Maybe your organization will want to stipulate that an employee would be eligible to win a prize once a quarter to give other employees a chance to win. Add the names of each submitter to a list for a prize drawing to be held at the end of the year or at an employee meeting. Send out emails with sample snapshots of the latest attacks, so others can avoid them.
- Staff are human; if someone makes an honest mistake, reward them for reporting it immediately. The sooner it gets turned in, the faster the issue can be resolved. Of course, the staff person needs to understand what happened and how to avoid it in the future. Organizational controls should also be reviewed to help avoid that issue in the future. Maybe a policy needs to be changed, some staff need retraining, or maybe a technical control can be added to eliminate the issue.
- Have a process for reporting lost or stolen devices that includes who to contact and how. Decide if the process should include automatic wiping of the device. Make sure that employees are aware of the process.
- Have a response plan for when a security issue is reported, whether an employee, a customer, a vendor, or a volunteer is the person reporting.. Ensure that a contact is always available for found security or privacy issues.
- Post a short list of actions for possible security and privacy issues in a prominent place like a break room or a kitchen. Also give the list to employees so they know what to do in an emergency.
People—your customers, your employees, your partners—make a security program work!
Oura ring review
Posted: October 28, 2018 by IntentionalPrivacy in Health DevicesTags: data integrity, exercise tracking, ouraring, sleep, sleep tracking, wearables, wellness
I purchased my Second-Generation Oura ring, a black Heritage, in December, 2017, and received it on September 5, 2018. I started wearing it on September 8, 2018. I have been wearing it now for about six weeks. I purchased it to replace my first-generation ring—also black—that I bought in January, 2017. People have frequently commented on how beautiful each ring was; even asking if the ring was made from hematite.
My review is for the Android application, Oura Cloud, and the Second-Generation Oura ring. I am using a Motorola Moto G5 Plus Android phone. With the first-generation ring, I used both the Moto and a Samsung Galaxy S5 Android phones. My provider has been Verizon for years.
How do I like the ring?
I used the ring sizer provided by Oura to determine the correct size. Ultimately, I purchased the same size as the First-Generation Oura ring. Each ring has been worn on my dominant hand. The Second-Generation Oura ring is smaller than the first ring and fits my index finger very snugly, so I usually wear it on my dominant hand ring finger. The ring is comfortable, but slides around on my ring finger. Because it slides around, it does not always collect an entire night’s data, particularly the heart rate information. I am sometimes suspicious that it is not collecting Sleep data correctly as well, and I have had multiple issues with Activity data. I did not have these issues with the first ring. Since First-Generation Oura ring had a bigger footprint and fit me better, it did not slide around my finger as easily.
⇒ Oura suggests:
Sometimes there can be gaps in the night-time resting heart rate and/or heart rate variability graphs. This usually means that something has interfered with the pulse signal, and the ring hasn’t been able to detect your heart rate.
Pulse signal tracking may be disrupted if the ring sits too loosely on your finger, and the ring sensors don’t have a good quality contact with your skin. The ring should sit comfortably but snugly enough, and the sensor bumps should be underneath your finger. You’ll find more information about wearing the ring in ring sizing FAQ. If the ring feels too loose at bedtime, try wearing the ring on a different finger or if kept in (sic) same finger, just before bedtime ensure the LED sensors are under your finger and slide it towards your knuckle for better snugness (to thicker part of your finger).
Body signal tracking can also be temporarily disturbed if the ring detects a lot of movement, or if you sleep in a position where your hand goes numb (partially blocked circulation).
There are situations where Oura may not show your resting heart rate and heart rate variability graphs properly, for example if your resting heart rate is exceptionally low (below 30 bpm) or you have exceptionally high HRV (respiratory sinus arrhythmia, or other arrhythmia).
⇒ Oura: Exactly how do you propose that I keep the ring from changing position on my finger while I’m asleep?
How accurate is the ring?
I have had multiple problems with the Second-Generation Oura ring’s data collection and accuracy. Some of the issues can be traced to the different units used and rounding issues. Imperial units should use the month-day-year format, miles, pounds, and Fahrenheit, while metric should be in day-month-year format, kilometers, kilograms, and Celsius. My opinion? Since the ring provides data for both imperial and metric units, collect it as one unit, do a conversion to the other if the customer wants it, and store both in the cloud so the customer can confirm that the data conversion is correct. Do a conversion only ONCE. Use column labels that indicate the units. Rounding to a specific number of digits should be consistent and across the board and part of the conversion. Remember: Just because a number has more digits does not make the number more accurate.
Doing a conversion only once also means that a customer will have a seamless continuity of data whether viewing it in the app or in the cloud, or downloading the data.
- Temperature can be accessed from four different places and has different values for what is supposed to be the same date and time. The graph scale does not match numbers and graph points. The graph scale is supposed to be .4 of a degree, but the bars do not match the scale values. Here is an example of how the data is not the same:
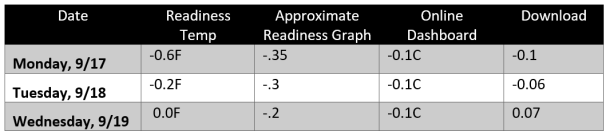
Recently, they have added labels to the graphs; even if the scale is not correct (which it is not currently), you see what it is supposed to be.
- Sleep: I do not understand how the app calculates the number of wakeups during the night. Sometimes it appears that the period of time for falling asleep and/or waking up is counted. Sometimes not. Sometimes I cannot find a pattern to what is being counted.
⇒ My suggestion: This ought to be transparent and easy to figure out or Oura ought to explain how they calculate this number.
- Sometimes there is a section on the Totals page called “Restful Periods.” Sometimes it is also displayed on the Readiness page. It does not appear every day, even on days when I do meditation or take a nap in the afternoon. Another issue is that when I try to look at that information again, it is not always available.
- In the Readiness section, Activity Balance and Recovery Index are two sections that do not make sense to me. It can show that your activity is optimal on the Activity page (Meeting Daily Targets, Move Every Hour, Training Frequency, Training Volume, Recovery Time, Activity Score –all good), but Activity Balance and Recovery Index are both red on the Readiness screen. The reasons should be explained.
- I have had multiple problems with my exercise showing up correctly in the Second-Generation Oura ring. I often use a walking exercise video to exercise with. For example, on September 13th, I used the video to finish a 2-mile walk. The app showed I had completed 0.5 miles of walking. My first Oura ring—after completing the same video (which I have used for years)—always showed a number much closer to 2 miles (sometimes a little more, sometimes a little less but always close). Another time, I was attending a class from 5:30 to 10 pm. The app Activity page showed exercise between high and medium around 8 pm in the App and high in the cloud dashboard. I assure you, I was sitting in a chair the entire time; we only had a couple of five-minute breaks all night.
I looked at my exercise for October 22 in Oura Cloud and then at the app on my phone. My phone showed 12 minutes of high activity while Oura Cloud shows three minutes, and the graphs shown in the Oura Cloud and in the phone app are not the same (see chart below):

⇒ Oura’s suggestion: To get the data to complete an upload from the ring to the phone app, do a force-quit of the application.
I have to do that just about daily. I also frequently reset the Bluetooth connection and even power cycle the phone to get the upload to function correctly. I have even reinstalled the application a couple of times. I also did a factory reset, which wipes the data from the ring.
Note: Make sure you manually back up all the data to the cloud before you attempt a factory reset.
For the First-Generation Oura ring, after they got the initial sync issues resolved, I could connect the app to the ring however far apart the phone and the ring were located in my home. The Second-Generation Oura ring claims to use Bluetooth Low-Energy Smart, which includes Ring Airplane mode. The theoretical distance for Bluetooth Low-Energy Smart is >330 feet. This app and the Second-Generation ring have difficulty connecting if the ring is two inches away and the app must have focus. Want to check your email while the ring and the app are syncing? Do not do it! And this ring often does not sync all 3 types of data at the same time (usually Activity syncs, but not Sleep nor Readiness) even when the phone is less than a foot away (next to the ring on the charger) and the app has focus, unless I do a force quit.
I am hoping that the last firmware update (0.40.2) that finally happened after trying for two weeks will fix some of the hardware issues that I have been experiencing.
- Sometimes it automatically uploads data to the Oura cloud, sometimes it does not.
⇒ My suggestion: add a time to the date that the last sync occurred so that one can ascertain precisely when the data sync last occurred.
- When I am done syncing the ring, I put the ring in Airplane mode, turn Bluetooth and Location off on the phone, and put it on my finger. On at least one occasion, the ring turned off Airplane mode when I was wearing it. According to Oura’s Troubleshooting documentation https://help.ouraring.com/about-the-new-oura-ring/ring-airplane-mode, the way to turn off Airplane mode is to place the ring in the ring charger. Sometimes the app shows Airplane mode (Location and Bluetooth are enabled on the phone), but it downloads the data to the phone app anyway.
- Sometimes they “fix” one issue only to break other working parts. One that was classic showed the same Sleep total when you moved from one date to another. In other words, when looking at Trends, the line was flat across several days (and Oura told me that could not be fixed). At the moment, sometimes totals move on the Sleep, Activity, or Readiness screens when the date is changed on those screens in the app, most often they do not.
- The battery life—right out of the box—did not last even 4 days, although technically it fits the parameter of “battery-life of up to a week.”
- Firmware updates to the ring take several tries before they work. Again, I tried doing a Force Restart before starting it, removing the Bluetooth connection and re-adding it, and even power cycling the phone. The option to update the firmware also did not appear every time the ring was synced; I was not sure if it was applied and just did not update in the app or if it really aborted the way the screen said.
- I am not seeing other features they promised:
- Circadian alignment guidance and optimal bedtimes
- Sleep improvement programs
- On-demand HR and HRV tracking for meditation or breathing exercise
Other issues:
Right after I received the new ring and before I set it up, Oura forced an application update (without any warning) to the “new” app. I lost a couple of days of data because I did not have the chance to back up the old ring to the cloud and the app did not do it automatically. This is a bad way to upgrade an application!
Another instance of sloppy data interchange: the Oura Cloud My Account page does not contain my personal information—(measurement) units, height, weight, age, gender (although each item has been filled in on the Oura app)—and does not allow me to change them.
⇒ My suggestion: If not necessary for use by the data in the cloud, this section (except measurement units) should be deleted. Personally, I would prefer (as stated above), that the imperial units be used for all my data.
Conclusion
Although I had problems with the First-Generation Oura ring syncing for about six weeks, I did not notice the other issues I have seen with the Second-Generation Oura ring. Overall, the Second-Generation Oura ring is very disappointing and yes, even frustrating.
In my opinion, the app is ready for beta testing only, not commercial release. There are too many issues between data accuracy, data reporting, and functionality. How can you trust data when the values do not match? How can you trust a device when it is not clear that Airplane mode is functioning correctly? Why can’t they improve data communication between the Oura app and the Second-Generation Oura ring?
According to Oura’s article, What’s different in body signal tracking between the first and the new Oura ring, I should be seeing more accuracy. I am NOT.
A way to discover when your data calculations are not correct without having to depend on your customers is to create an Excel spreadsheet with your data points (preferably from beta testers) and then hand calculate the data points. Then, have someone else hand calculate to ensure that the calculations are the same. If they are not, discover what caused the discrepancy. Then put the calculations in Excel. Compare. The data points should be the same whether you use an Android or an iPhone as the data in Oura Cloud. It is not rocket science!
Oura does not provide adequate quality assurance testing. Fixing one problem should not break another part of the app.
Oura has assured me that the iPhone app does not have the issues that I have seen with the Android app. One of the customer reps told me that he has an Android phone and testing is more difficult for the Android because of the wide variety of phones. Yes, I can understand that. But the way to fix that is to keep track of bugs encountered between various Android phones and providers and create edge cases. Using a wish-and-a-prayer approach to managing a data project does not work.
I have offered on a number of occasions to be a beta tester and/or help them with their quality assurance program. They did not accept. I have asked for a timeline for when these bugs will be resolved. No timeline has been forthcoming.
If Oura had told me the ring would be in beta testing when I received it, I might have waited to buy it or I might have happily participated. I think they should have given me the option. I bought it in December; it was supposed to start shipping in April. I did not receive mine until September. They are blaming the production issues on a supplier. Supplier issues should be covered by contract penalties. However, it seems like Oura could have worked out a number of bugs in that time frame.
The idea behind the Oura ring is amazing! However, based on its current implementation with the Android, I cannot recommend the Second-Generation Oura ring to anyone nor will I be purchasing any future technology from them.
Data Privacy Day 2018!
Posted: January 26, 2018 by IntentionalPrivacy in Data Privacy DayTags: Data Privacy Day, StaySafeOnline.org
Here are some resources from StaySafeOnline.org to help protect your and your family’s privacy online.
New Year’s Resolution: Find Your Blind Spot!
Posted: January 1, 2018 by IntentionalPrivacy in Automobile hacking, Cell phone, Ethics, Issues, New Year's Resolutions, Privacy, Theft, VulnerabilitiesTags: #FindYourBlindSpot, Computer Forensics, Ethics, New Year's Resolutions
Today is New Year’s Day, a day typically devoted to hangovers and making resolutions.
I recently saw a presentation about automotive computer forensics that made me think about New Year’s resolutions. In spite of my background in computer forensics, I had not considered that automotive computers were advanced enough to conduct forensic investigations on. I enjoyed the presentation and I seriously considered taking the class even though it would not advance my career in Texas.
But then the instructor ruined the class for me by doing two things.
The first was when the presenter—an instructor for a world-famous IT school—talked about driving his yellow muscle car at 65 MPH in a 15-MPH school zone and getting a ticket.
Does he use the ticket as an agent of change? Take his punishment? Learn to drive his car on a racetrack?
No, he was standing up there bragging about his yellow car and getting away with driving fast in a school zone. He is just like those rich-and-powerful gropers that have been lately in the news. They do it because they can and because they (at least used to) get away with it. I do not admire them and I do not admire him.
I appreciate that traffic tickets are expensive (particularly tickets in a school zone), that such a ticket would cause the recipient’s insurance rates to go through the roof, that such a driver might be required to attend traffic school, and that there might be other consequences. I understand the desire to avoid those consequences. I understand that he has a legal right to hire an attorney who will reschedule the court hearing until the police officer could not attend.
Since the police officer could not attend, the ticket was dismissed.
When he was talking about this experience, I was nodding right along with everyone else, but on the way home, I started thinking about what he said and who he is. This presenter possesses several certifications (such as a CISSP), many of which require the possessor to agree to abide by strict ethical standards. In fact, (ISC)2, the certifying body of the CISSP certification, issues just such a code of ethics. The relevant portion is listed below:
Code of Ethics Preamble:
- The safety and welfare of society and the common good, duty to our principles, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.
- Therefore, strict adherence to this Code is a condition of certification.
Code of Ethics Canons:
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Act honorably, honestly, justly, responsibly, and legally.
- Provide diligent and competent service to principles.
- Advance and protect the profession.
Driving 50 miles above the speed limit obviously breaks several of those tenets (even though this situation was probably not what (ISC)2 had in mind). Another problem I have with his crazy driving is that this man appeared to be in his late sixties. Does he have the reflexes necessary to drive like this?
How far does a car going 65 mph travel before coming to a complete stop? According to Government-Fleet.com, “it takes the average driver from one-half to three-quarters of a second to perceive a need to hit the brakes, and another three-quarters of a second to move your (sic) foot from the gas to the brake pedal. Nacto.org states that “… if a street surface is dry, the average driver can safely decelerate an automobile or light truck with reasonably good tires at the rate of about 15 feet per second (FPS).” Let’s examine how that plays out.

To put this in perspective, a football field is 300 feet long from goal post to goal post. A vehicle traveling 65 MPH (given average conditions) will take 396 feet to stop—more than the length of a football field!
The laws of physics apply to everyone. It does not matter how well you drive. If a six-year-old child steps in front of a vehicle traveling 65 MPH, he or she is dead. If the vehicle is traveling 15 MPH, the kid at least has a chance to learn a lesson.
The second thing he said that I had an issue with was when he was talking about how vehicle forensics is now appearing in court cases. As an example, he talked about a case in Texas where a minister regularly connected his phone to the car infotainment center over Bluetooth, which meant that things maintained on the phone such as contacts and photos are transferred to the car’s computer. He claimed that even if a picture is deleted from the phone, it stays on the vehicle computer. When the preacher took his car into the dealership for service, some of the dealership’s service people stole nude pictures of the clergyman’s wife from the car’s infotainment computer and posted them on a swingers’ site as a joke. One of the preacher’s parishioners told him about the pictures being posted. The clergyman and his wife were understandably upset about this and were suing the dealership.
Since I wanted to write an article for this blog about vehicle computer forensics and the amazing amount of information that can be obtained from an automobile’s computer systems, I looked for articles about that incident.
Except the articles I found about a Texas preacher whose wife’s nude pictures were posted on a swingers’ website had nothing whatsoever to do with the vehicle’s infotainment computer. The photos were stolen from the customer’s phone. When I realized that he had twisted the story to fit his theme, I was appalled.
What really happened: A preacher and his wife went to a Dallas Toyota dealership to buy a car. The minister had gotten a preapproval for the loan from an app on his phone. The salesman took the customer’s phone to show the manager the preapproval. While the salesman was out of sight, he found some nude pictures of the wife on the phone and emailed them to himself and the swingers’ site. Then erased the email. The couple were outraged—rightly so!—about this intrusion into their privacy and the theft of pictures of a “private moment.” They hired attorney Gloria Allred to sue Toyota, the Dallas dealership, and the car salesman. You can read more about it here.
A computer forensics professional is required to present the facts fairly and accurately. Given these two stories, would you trust this man to represent the facts fairly and accurately? Would you trust him to act ethically and honorably?
I am asking you to add these New Year’s resolutions to your list this year:
- Drive the speed limit. Drive as if it could be your child, your grandmother, or your dog in that crosswalk!
- Check the accuracy of your information before you give a presentation. Give citations, so that other people can verify your work. If I am in the audience, I will.
- Find your blind spot and change it to something positive.
- Do not allow anyone access to your phone, especially if that person is out of your sight.
Have a wonderful new year!
References
“Driver care: Know Your Stopping Distance,” http://www.government-fleet.com/content/driver-care-know-your-stopping-distance.aspx
“Vehicle Stopping Distance and Time,” https://nacto.org/docs/usdg/vehicle_stopping_distance_and_time_upenn.pdf
“Couple Sues Grapevine Car Dealership Claiming Salesman Shared Their Photos on a Swingers Site,” http://www.dallasobserver.com/news/couple-sues-grapevine-car-dealership-claiming-salesman-shared-their-photos-on-a-swingers-site-8957090
“Texas pastor claims Toyota car salesman stole his wife’s nude photos and emailed them to a swingers’ site,” http://www.dailymail.co.uk/news/article-3994292/Texas-pastor-claims-Toyota-car-salesman-stole-wife-s-nude-photos-emailed-swingers-site.html
Credit freeze vs Credit lock – which is best?
Posted: October 4, 2017 by IntentionalPrivacy in Equifax, EquiMess, Security Breach, VulnerabilitiesTags: breach response, credit bureaus, credit freeze, credit lock, data brokers, Equifax breach, former Equifax CEO Smith
Equifax and the other credit bureaus are trying to convince consumers to put “credit locks” on their credit files instead of credit freezes. Credit locks are – I think – a really bad, bad idea. Why?
- Why would you trust anything a company tells you that did not encrypt a database with 145 MILLION records in it? Former Equifax CEO Smith testified yesterday at the House of Representatives that Equifax has a poor record of encrypting data. To read the latest about the EquiMess, click on Wired‘s “6 Fresh Horrors From the Equifax CEO’s Congressional Hearing.” Talk about dancing on the head of a pin!
- The credit bureaus claim a lock is “free” and simple to use through an app on your phone … the problem is that nothing is free, and again, why would anyone trust them? They’re selling your information somehow to pay for that lock.
- What’s the difference between a lock and a freeze? Well, nobody seems to know. While credit freezes have a cost to set up and remove (which varies from state to state), they’re regulated by state and federal law. When you sign up for a freeze, you do not have to agree to arbitrary credit bureau terms and conditions (such as giving up your right to sue or participate in class-action law suits).
More on credit freezes vs credit locks: “Myths vs. facts: Sorting out confusion surrounding Equifax breach, credit freezes.”
Equifax Happened: What Are We Going to Do About It?
Posted: October 3, 2017 by IntentionalPrivacy in Financial vulnerabilities, Security BreachTags: breach response, data brokers, Equifax breach
I have been doing a lot of thinking about Equifax. You can point fingers and say … well, you can say all kinds of things. Equifax should have patched faster, they should have notified faster, they should have been more organized about their response, they should have spent more money on security … While every one of those statements are true, they do not resolve the problem of breach response. They will not prevent future breaches. They do not make us safer.
What is going to make us safer?
What have we learned from all these breaches? What will keep our information safe going forward? That is what really matters. What happened in the past only matters if we learned something from it (unless you are an attorney running a class-action lawsuit or, God forbid, your identity was stolen).
Regulations
Should the US implement regulations like the European Union’s General Data Protection Regulation (GDPR)? Will more regulation make us safer?
There’s no doubt we need better regulations and oversight, especially on data brokers. There are more than 2500 data brokers in this country; your information is their product. For the most part, you cannot opt out and you cannot control what data brokers do with it. And if your file contains errors, chances are you will not be able to correct those errors. For an interesting overview of data brokers, read Privacy Rights Clearinghouse’s article “Data Brokers and ‘People Search’ Sites.”
Won’t automation or lots of expensive tools keep us safer?
Part of the problem is that big companies in particular want to throw technological solutions at data security. Maybe technological solutions make the board feel safer. Maybe they cannot find personnel. Maybe it is because people are expensive.
Layers of security
When an organization gets breached because they did not patch or no one was paying attention to alerts, management may be surprised because they thought spending money on expensive tools would save them from breaches. The vendors say it was not their fault because the tools were not correctly implemented. The staff says they did not get training or they were testing it or it does not work the way it is supposed to or there were too many extraneous alerts.
Organizations need tools, but their focus should be on the basics. Organizations should know how their data flows: how it comes in, where it goes internally, and when and where it leaves. Private personal information (PPI) should be encrypted whether it is moving or at rest. Organizations should know what and where their assets are. They should understand that employees are going to make mistakes and plan for them. Back up, disaster recovery, and redundant systems are necessary. Flat networks are a disaster waiting to happen: put things in security zones and implement authorization and authentication practices. Enact user training. Be careful who has administrative privileges. Practice safe passwords. Implement policies and procedures and physical security.
Security people know these layers; management should know and understand them also.
